
Landing zone architectures and cloud security
Using a packaged architecture to deliver key controls.
Read more
Using a packaged architecture to deliver key controls.
Read more
A plain English summary of ISO 27000.
Read more
Information security governance without starting from scratch.
Read more
There’s more than one way to do it.
Read more
The principles that effective architectures should follow.
Read more
Same use case, new implementation.
Read more
Explaining a common misconception.
Read more
How secure is your EKS cluster? Check it with kube-bench.
Read more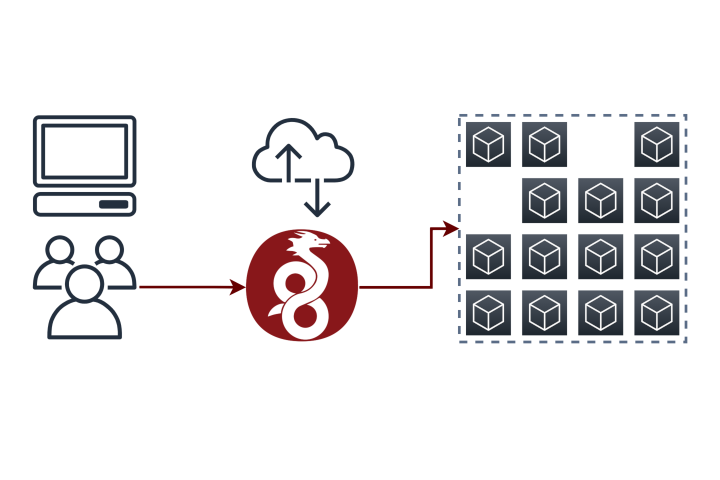
A fresh take on VPN implementation.
Read more