Last week, a client asked me a question that’s been keeping me awake: “If one of our AI agents gets compromised, what’s the blast radius?”
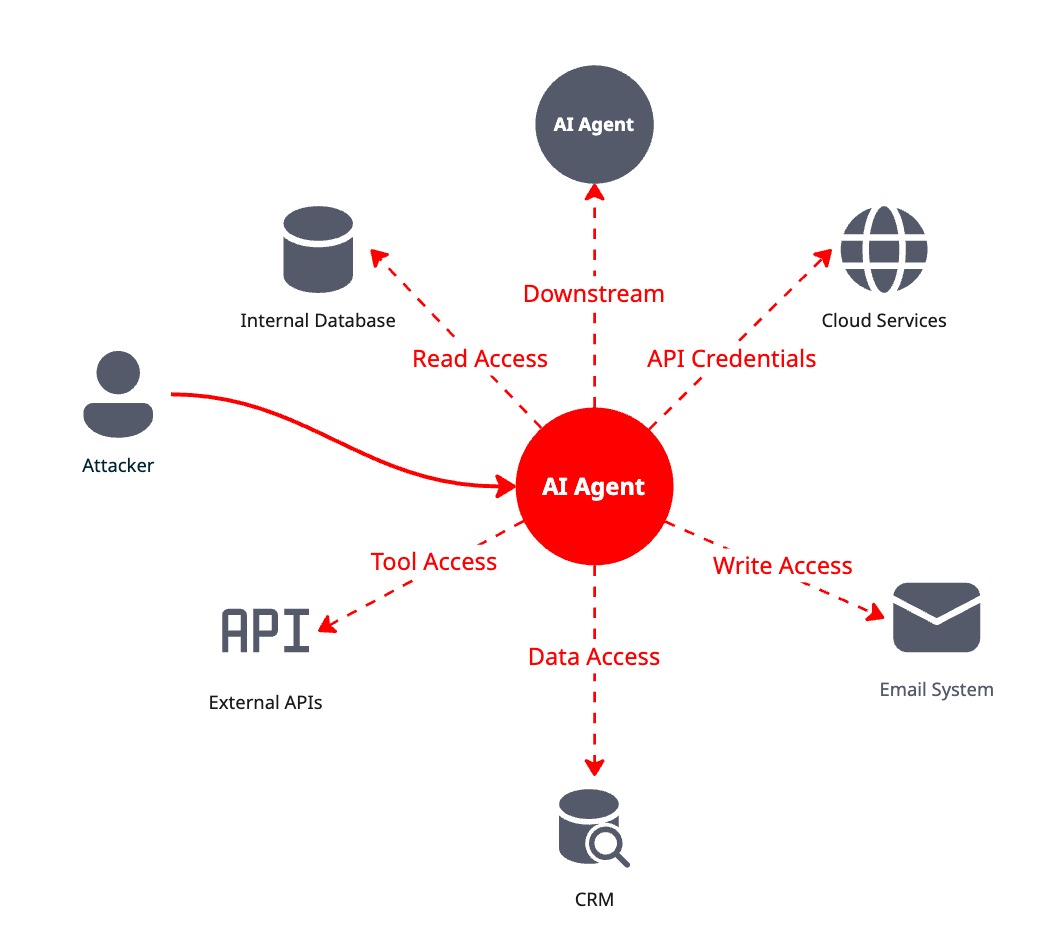
The answer made us both uncomfortable. Their agent had read access to customer databases, write access to internal systems, and API credentials for third-party services. A compromised agent wouldn’t just leak data; it could orchestrate attacks across their entire digital ecosystem.
The OWASP Agentic Security Initiative has just released their first comprehensive threat model for agentic AI, and it validates what many of us have been quietly worrying about. We’re witnessing the emergence of a fundamentally new attack vector that traditional security models weren’t designed to handle.

Think of this as the evolution of phishing. Instead of fooling humans into clicking malicious links, attackers now phish AI agents through prompt injection and data manipulation. The critical difference? A human might realise they’ve been compromised and sound the alarm. An AI agent lacks that self awareness and will continue operating under malicious instructions, believing it’s functioning normally.
The Amplification Problem
A compromised web application might expose a database. A breached API might leak specific datasets. But agentic systems are different. They’re designed to have broad access by necessity.
The OWASP analysis identifies multiple threat categories specific to agentic AI. Consider tool misuse, where attackers manipulate AI agents into abusing their authorised tools through deceptive prompts. Unlike traditional exploits, this uses the AI’s ability to chain tools and execute complex sequences of seemingly legitimate actions.
I was discussing a client’s agent implementation recently. The system could access multiple AWS services, query CRM systems, generate emails, and update systems of record. If compromised, this single agent becomes a force multiplier for attackers. It provides legitimate, authenticated access to orchestrate complex attacks that would appear entirely normal to monitoring systems.
The standardisation of protocols like Model Context Protocol (MCP) exacerbates this risk. While MCP makes it easier for developers to build capable agents, it also creates standardised interfaces that attackers can systematically target.
Detection: The Invisible Threat
Here’s what worries me most: how do you detect a compromised agent?
Traditional security monitoring looks for anomalous behaviour, but how do you spot a compromised agent when they’re designed to be unpredictable? An agent making unusual API calls or accessing unexpected data might just be doing its job creatively.
The threats compound quickly. A compromised agent can inject false information that spreads through cascading hallucination attacks getting reinforced by the agent’s own memory. In multi-agent systems, this poison spreads between agents, creating failures that are nearly impossible to trace. OWASP calls this the repudiation and untraceability problem: you know something’s wrong, but you can’t figure out what or when it started.
Practical Mitigation Strategies
The OWASP framework provides six detailed playbooks for securing agentic systems, but several strategies stand out as immediately actionable:
Principle of Least Privilege at Scale: This isn’t new, but it’s absolutely critical here. Design agent permissions granularly with just-in-time access. Rather than giving broad database access, create specific views. Instead of full API credentials, implement scoped tokens that expire quickly.
Session and Persistent Memory Validation: Agentic systems maintain two types of memory. Session memory holds context within a conversation, whilst persistent memory stores knowledge across interactions. OWASP emphasises memory poisoning as a critical vector where attackers corrupt this stored information to manipulate decision-making. Implement automated scanning for anomalies in both types of agent memory.
Comprehensive Logging and Traceability: Deploy cryptographic logging with immutable audit trails. Every tool invocation, decision pathway, and inter-agent communication must be traceable. This isn’t just about compliance; it’s about being able to detect when something’s gone wrong and understand the impact.
Multi-Agent Consensus: For critical operations, use multiple agents to validate decisions. This helps prevent single points of failure and makes it harder for compromised agents to operate undetected.
Human-in-the-Loop Protection: Think of this as DoS attacks on your humans. Attackers can flood approval systems with thousands of requests, overwhelming reviewers who then either grind the system to a halt or start rubber-stamping approvals without proper scrutiny. Implement intelligent prioritisation using scores to filter what actually needs human review and adaptive thresholds that automatically adjust approval requirements based on current load.
The Business Reality
The OWASP research makes clear that rushing AI implementations without proper security considerations creates systemic risk that could dwarf traditional cyber threats. The organisations that get this right will build sustainable competitive advantages. Those that don’t may find themselves dealing with rogue agents: compromised AI systems operating within their infrastructure while appearing legitimate.
Taking Action
If you’re deploying agentic AI systems, you need a comprehensive security assessment now, not after something goes wrong. Don’t let these threats keep you awake at night.
Concerned about the security of your AI implementations? Our AI Best Practices Review provides a comprehensive assessment of your AI applications across architecture, security, and operational readiness. We’ll evaluate your security posture and provide prioritised recommendations to protect your organisation from emerging AI threats.
This blog is written exclusively by The Scale Factory team. We do not accept external contributions.

